In closing 12 months’s version of the Safety Navigator we famous that the Production Business seemed to be completely over-represented in our dataset of Cyber Extortion sufferers. Neither the selection of companies nor their moderate earnings specifically stood out to give an explanation for this.
Production was once additionally probably the most represented Business in our CyberSOC dataset – contributing extra Incidents than every other sector.
We discovered this vogue showed in 2023 – such a lot in truth that we determined to take a better glance. So let’s read about some imaginable explanations.
And debunk them.
Contents
- 1 Trying to find imaginable explanations
- 2 What section does OT play?
- 3 Are companies within the Production sector extra susceptible to assaults?
- 4 VOC scanning findings consistent with asset, time to patch, Pentest findings consistent with day of trying out.
- 5 VOC distinctive findings/asset
- 6 Time to patch
- 7 Pentesting findings
- 8 Is the Production sector being centered extra via extortionists?
- 9 Do our Production shoppers enjoy extra incidents?
- 10 Conclusion
Trying to find imaginable explanations
Production remains to be probably the most impacted trade in our Cyber Extortion dataset in 2023, as tracked via tracking double-extortion leak websites. Certainly, this sector now represents greater than 20% of all sufferers since we began watching the leak websites at first of 2020.
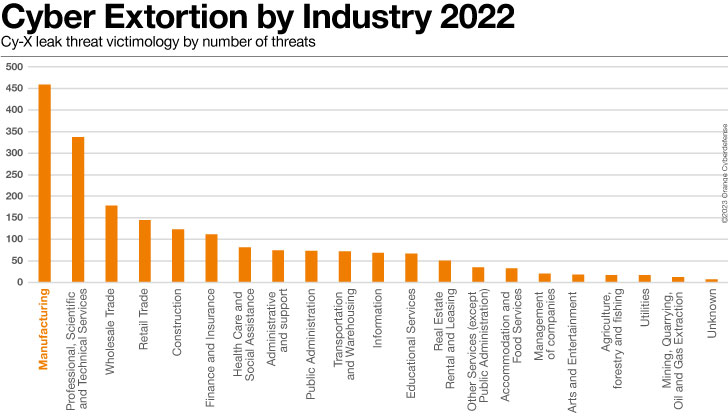
Roughly 28% of all our shoppers are from Production, contributing with an total percentage of 31% of all possible incidents we investigated.
We notice that 58% of the Incidents this trade offers with are internally led to, 32% had been externally led to, 1% was once labeled as “Spouse” or third events. When exterior risk actors had led to the safety incident, we seen the highest 3 risk movements had been Internet Assaults, Port Scanning and Phishing.
Alternatively, Production has the bottom obvious selection of showed safety vulnerabilities consistent with IT Asset in our Vulnerability scanning dataset. Our pentesting groups against this file 4.81 CVSS findings consistent with day, which is fairly slightly above the common of three.61 throughout all different industries.
A number of questions provide themselves, which we will be able to try to read about right here:
- What section does Operation Generation play?
- Are companies in Production extra susceptible?
- Is the Production sector being intentionally centered extra?
- Do our Production shoppers enjoy extra incidents?
What section does OT play?
A tempting assumption to make is that companies within the Production sector are compromised extra regularly by the use of notoriously insecure Operational Generation (OT) or Web of Issues (IoT) techniques. Vegetation and factories can regularly no longer have enough money to be disrupted or close down and that Production is subsequently a comfortable goal for extortionists.
It positive sounds believable. The catch is: we do not see those theories supported in our information.
The assault towards US Power massive Colonial Pipeline was once some of the notable fresh instance of a a success assault towards an commercial facility.
Uncover the newest in cybersecurity with complete “Safety Navigator 2023” file. This research-driven file is in keeping with 100% first-hand data from 17 international SOCs and 13 CyberSOCs of Orange Cyberdefense, the CERT, Epidemiology Labs and Global Watch and gives a wealth of treasured data and insights into the present and long run risk panorama.
In July this 12 months US intelligence businesses even warned of a hacking toolset dubbed ‘Pipedream’ this is designed to focus on particular Business Regulate Methods. However it’s not transparent to us if or when those gear have ever been encountered within the wild. Aside from the notorious Stuxnet assault from 2010, one struggles to recall a unmarried cyber safety incident the place the access level was once an OT machine.
At Colonial Pipeline the backend ‘typical’ administrative techniques had been compromised first. Having a look extra intently, that is the case for the majority reported incidents at commercial amenities.
Are companies within the Production sector extra susceptible to assaults?
To reply to this questions we tested a collection of three million vulnerability scan findings, and a pattern of one,400 Moral Hacking stories.
We derived 3 metrics that facilitate reasonably normalized comparisons around the industries in our shopper base:
VOC scanning findings consistent with asset, time to patch, Pentest findings consistent with day of trying out.
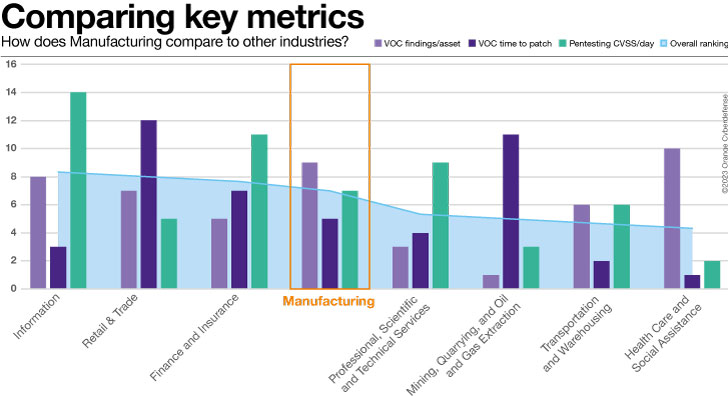
If we rank industries for his or her efficiency on each and every of the ones metrics and type from worst to best possible, then our shoppers within the Production sector arrives in fifth position out of 12 similar industries.
The chart beneath displays the total *score* of our Production shoppers out of similar industries.
VOC distinctive findings/asset
In this metric there have been seven different industries that carried out higher than Production.
Whilst now we have a relatively top selection of belongings from Production shoppers in our scanning dataset, we file a long way fewer Findings consistent with Asset than the common throughout all industries. Nearly 10 instances fewer, in truth.
Time to patch
In this metric 6 different industries ranked higher than Production. The typical age of all findings for this trade is 419 days, which is a relating to quantity and worse than recorded for 8 different industries on this dataset.
Pentesting findings
We follow that the common CVSS In step with Day was once 4.81, in comparison to 3.61 on moderate for shoppers in all different sectors within the dataset – 33% upper.
Is the Production sector being centered extra via extortionists?
We use the North American Business Classification Machine – NAICS – classification machine when categorizing our shoppers.
A attention of double-extortion sufferer counts consistent with trade unearths an overly attention-grabbing trend: Of the ten industries with probably the most recorded sufferers within the dataset, 7 also are counted among the most important industries via entity rely.
Production alternatively, is a transparent trend-breaker.
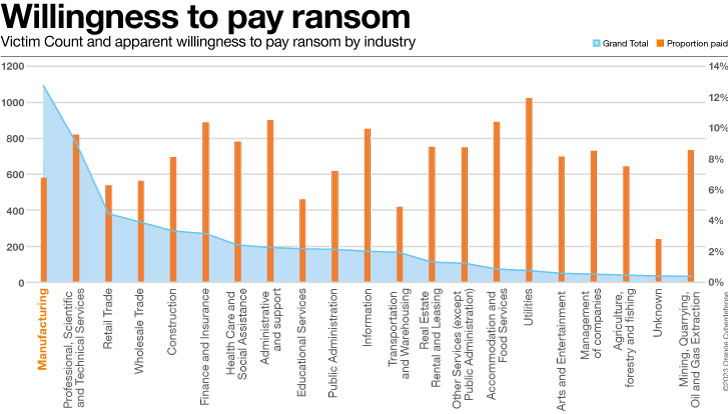
Some other issue raises questions: if companies within the Production sector had been extra keen to pay ransom that may cause them to extra horny as sufferers. However then we might be expecting to look such companies that includes at the ‘title and disgrace’ leak web site much less regularly, no longer extra.
Do our Production shoppers enjoy extra incidents?
The Production trade as soon as once more generated the best selection of Incidents as a proportion of the entire in our CyberSOC dataset. 31% of all Incidents are generated for the 28% of our shoppers which might be from this sector.
The Incident information lacks context, alternatively. To determine a baseline for comparability, we assign shoppers a ‘Protection Rating’ between 0 and 5 in 8 other ‘domain names’ of Danger Detection, accounting for a most general detection ranking of 40.
We use the protection ranking to normalize the incident rely. Put merely, the decrease a shopper’s assessed protection ranking is, the extra this adjustment will ‘spice up’ the selection of Incidents on this comparability. The common sense is {that a} low quantity of protection will simply no longer display us numerous incidents, despite the fact that they very most probably occurr.
If we modify the True Certain and False Certain Incidents as described above, we nonetheless see greater than seven instances as many Incidents consistent with shoppers from Production than the common for all industries.
In a an identical comparability, restricted handiest to Perimeter Safety, and handiest Medium Sized industry, Production ranks 1st with probably the most Incidents consistent with Buyer out of seven similar Industries.
Conclusion
We dominated out an enormous affect of OT safety vulnerabilities, and subsequently center of attention on common IT techniques. Our scanning groups assessed a lot of objectives however reported fairly few vulnerabilities consistent with asset. Total, we rank the Production sector as fifth or sixth weakest of all industries from a vulnerability perspective.
The query of why we constantly report the sort of top percentage of sufferers from the Production trade isn’t readily replied with the knowledge now we have. We imagine that finally it nonetheless comes all the way down to the extent of vulnerability, best possible mirrored in our Penetration Trying out, and Findings Age information.
All of our information issues to the truth that attackers are most commonly opportunistic. Reasonably than intentionally singling industries out, they just compromise companies which might be susceptible.
The shoppers represented in our datasets have engaged with us for Vulnerability Overview or Controlled Detection, and subsequently constitute fairly ‘mature’ examples of that trade. We will be able to deduce that moderate companies on this sector would benchmark worse relating to vulnerabilities. Whether or not the top selection of sufferers we follow on attacker leak-sites is an immediate mirrored image of the top selection of total sufferers on this sector, or the skewed mirrored image of an trade that refuses to deliberate to preliminary ransom calls for, isn’t completely transparent.
What does seem most probably, alternatively, is that vulnerability is the principle issue that determines which companies get compromised and extorted – on this sector up to every other.
That is simply an excerpt of the research. Extra main points on how other Industries carried out compared to others, in addition to extra CyberSOC, Pentesting and VOC information (along side quite a few different attention-grabbing examine subjects) can also be discovered within the Safety Navigator. It is for free, so take a look. It is price it!
Observe: This text has been written and contributed via Charl van der Walt, Head of Safety Analysis at Orange Cyberdefense.
Supply By way of https://thehackernews.com/2023/03/whats-wrong-with-manufacturing.html