A prior to now undocumented danger actor dubbed YoroTrooper has been focused on govt, power, and world organizations throughout Europe as a part of a cyber espionage marketing campaign that has been energetic since no less than June 2022.
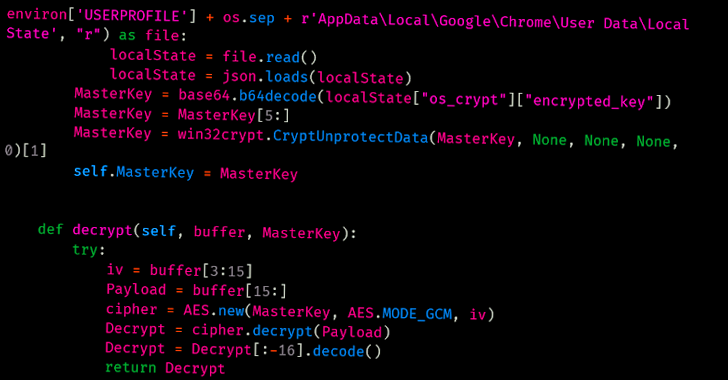
“Data stolen from a hit compromises come with credentials from more than one programs, browser histories and cookies, gadget knowledge and screenshots,” Cisco Talos researchers Asheer Malhotra and Vitor Ventura mentioned in a Tuesday research.
Outstanding international locations focused come with Azerbaijan, Tajikistan, Kyrgyzstan, Turkmenistan, and different Commonwealth of Impartial States (CIS) international locations.
The danger actor is thought to be Russian-speaking owing to the victimology patterns and the presence of Cyrillic snippets in one of the most implants.
That mentioned, the YoroTrooper intrusion set has been discovered to show off tactical overlaps with the PoetRAT workforce that used to be documented in 2020 as leveraging coronavirus-themed baits to strike govt and effort sectors in Azerbaijan.
YoroTrooper’s knowledge amassing targets are learned thru a mixture of commodity and open supply stealer malware comparable to Ave Maria (aka Warzone RAT), LodaRAT, Meterpreter, and Stink, with the an infection chains the use of malicious shortcut information (LNKs) and decoy paperwork wrapped in ZIP or RAR archives which might be propagated by means of spear-phishing.
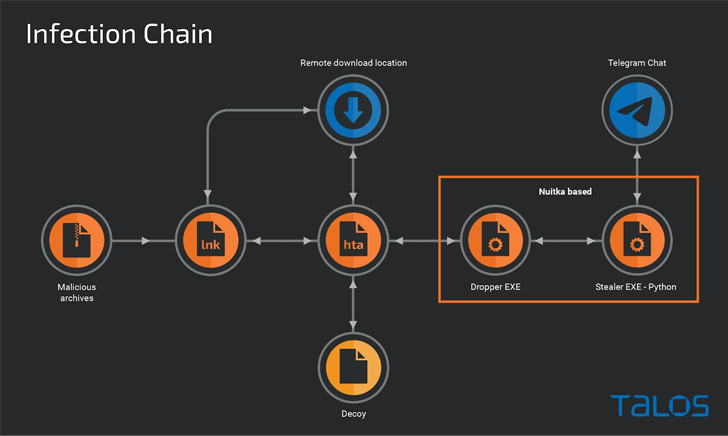
The LNK information serve as as easy downloaders to execute an HTA document retrieved from a far off server, which is then used to show a entice PDF record, whilst stealthily launching a dropper to ship a customized stealer that makes use of Telegram as an exfiltration channel.
0 Believe + Deception: Be told How one can Outsmart Attackers!
Uncover how Deception can come across complicated threats, forestall lateral motion, and support your 0 Believe technique. Sign up for our insightful webinar!
The usage of LodaRAT is notable because it signifies that the malware is being hired by means of more than one operators in spite of its attribution to every other staff known as Kasablanka, which has additionally been noticed distributing Ave Maria in contemporary campaigns focused on Russia.
Different auxiliary gear deployed by means of YoroTrooper include opposite shells and a C-based customized keylogger that is in a position to recording keystrokes and saving them to a document on disk.
“It’s price noting that whilst this marketing campaign started with the distribution of commodity malware comparable to Ave Maria and LodaRAT, it has advanced considerably to incorporate Python-based malware,” the researchers mentioned.
“This highlights an building up within the efforts the danger actor is setting up, most likely derived from a hit breaches right through the process the marketing campaign.”
Supply By way of https://thehackernews.com/2023/03/yorotrooper-stealing-credentials-and.html

